Since 2018, ACTSmart has been in partnership with Huntress Labs. Huntress is a team of engineers that finds security issues missed by anti-virus, firewalls, spam filters and DNS monitoring. In their initial test demonstration, they found hidden breaches in our test clients.
Why do you need this?
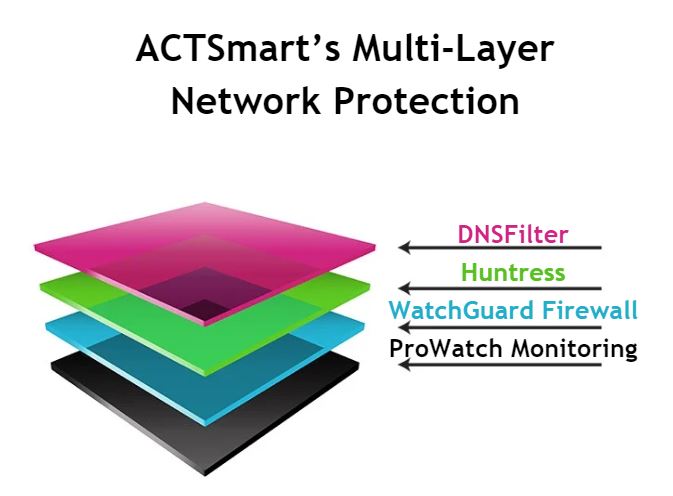
Unfortunately, the threat landscape dramatically shifted in 2016 when hackers realized small businesses could be as lucrative as well-guarded enterprises. If recent headlines have taught us anything, it’s that a determined hacker can bypass even the most robust security programs. In response, ACTSmart added more layers of protection as the threats became more treacherous.
Huntress started as a threat detection program that hunts for the unaddressed techniques hackers use to maintain access to their victims. Developed by former NSA (National Security Agency) Cyberwarfare Operators, their detection and response services give our clients another layer of security. Huntress has a team of well qualified engineers who actively hunt down threats that may have slipped past other layers of protection. This approach uncovers hackers abusing trusted applications and built-in Windows features that can evade detection for months. (See below for more information)
Back to our test demonstration… we were stunned to see several computers come back with active infections! These computers already had a robust antivirus, were protected by Open DNS to ensure safe web browsing and, they were all behind a powerful firewall! None the less, in one way or another, these threats were able to get a foothold on these computers until Huntress discovered these “ticking timebombs”.
Using Huntress’ expertise, ACTSmart is able to detect and eliminate these threats faster than ever before. It is for this reason that we strongly believe that every client needs this additional layer of security. We feel so strongly that we are requiring any client that declines this offer must sign off that they realize the importance of the protection that they are refusing.
ACTIVE THREAT HUNTING
Each week, headlines highlight massive data breaches. The one thing they all have in common is the victims’ dependency on the same old layers of security. We chose to fight back and invented a proactive new approach called Manages Detection and Response.
DEFENSE REIMAGINED
There’s no getting around it: cyber attackers are growing increasingly sophisticated in their tactics. From web apps and operating systems to hardware and human error, today’s hackers leave no potential vulnerability unchecked. But that’s why you have antivirus, right? Not so fast…
HUNT OR BE HUNTED
The threat landscape has changed. Traditional endpoint and network security products simply aren’t enough to protect the modern enterprise. After all, most of these offerings have just expanded on the same frameworks that hackers have successfully exploited for years. So what do you do? You hunt, or be hunted.