October is Cybersecurity Awareness Month, and we’re proud to join this global initiative to help educate and empower our employees, customers, and community on how to stay safe online.
In today’s digital world, cybersecurity isn’t just an IT concern, it’s everyone’s responsibility. Whether it’s protecting our company’s data, safeguarding customer information, or keeping our personal accounts secure, small actions make a big difference.
This year’s theme, “Stay Safe Online,” is a reminder that good cyber habits don’t have to be complicated or intimidating. Cybersecurity is achievable for everyone, and we’re here to support you in building confidence and awareness around the steps you can take to protect yourself and your organization.
Creating a cybersecurity culture in a small business isn’t about one big training session or a thick policy binder—it’s about making security part of everyday thinking, just like locking the door when you leave for the night. Here’s a roadmap that works especially well for small teams:
- Lead From the Top
- Owners, managers, and team leaders need to model good cyber habits. If leadership takes security seriously—using strong passwords, avoiding risky shortcuts, and speaking about it often—employees will follow.
- Keep Training Simple & Ongoing
- Short, regular tips (like your “Security Smarts” or snack-sized reminders) are better than once-a-year marathon sessions.
- Use real-life examples—like phishing emails you’ve actually seen in the wild—to make it relevant.
- Celebrate when employees spot and stop a scam.
- Make Security Part of the Job
- Write security into job roles: “Part of everyone’s job is protecting our data.”
- Create checklists for common tasks (logging in remotely, handling client files, updating software).
- Encourage employees to pause and ask if something seems suspicious—better a question than a breach.




Build on the basics and level up with these additional practices.
- Use Logging on Your Systems: Log activity so your team can monitor signs that threat actors may be trying to access your systems. Learn how to monitor key information.
- Back Up Data: Incidents happen, but when you back up critical information, recovery is faster and less stressful. Put a backup plan in place that aligns with your organization’s recovery point objective to protect your systems and keep things running smoothly.
- Encrypt Data: Encrypting your data and devices strengthens your defense against attacks. Even if criminals gain access to your files, information stays locked and unreadable. Make encryption part of your security strategy

| MYTH | REALITY |
| Don’t use a password manager because all your passwords are compromised if it gets hacked. |
Because of the technology password managers use, the company doesn’t even know your master password. So make it a long and unique password! And when you turn on MFA on your password manager, it’s even more secure. Even when a password manager company gets hacked, cybercriminals can’t access your passwords. |
| My spreadsheet/notes app/notebook is safer than a password manager. | No other method of storing passwords is as safe as a password manager because of its encryption. Physical notebooks and sticky notes can be lost, damaged, or stolen. Password managers also let you create long, complex, and unique passwords easily for every online account. With other methods, you’ll likely reuse passwords or depend on short, less random ones. |
| Password managers are expensive and hard to use. |
The leading brands of password managers all have free versions, and they have the same security features as the paid versions. Once you start using a password manager as a web browser extension, you’ll see how simple they are to incorporate into your web surfing. |
| My workplace won’t let me use a password manager. | Many workplaces use password managers now — ask your security or IT team what they recommend. Even if your workplace doesn’t have a password manager, you should definitely use one for your personal accounts. |
You have a lot of passwords, but you can start small! Research your password manager options, install one you like, and start adding a few passwords at a time. The program will help you change weaker passwords and create great passwords for new accounts.
Take a few minutes today and get started — your online safety is worth it!
OUR FAV PASSWORD MANAGER SETTINGS:
- MFA: Enabled
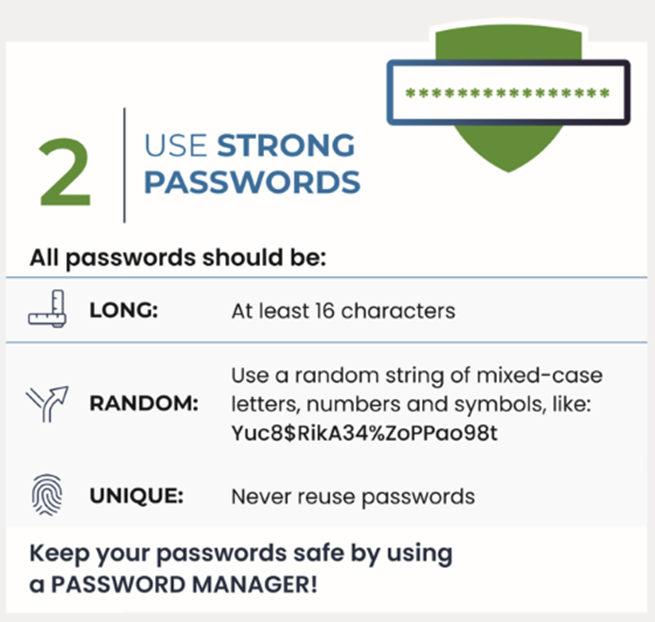
- Minimum password length: 16 characters
- Recovery codes: Saved in a safe place (like a safe!)

Online scams are becoming increasingly sophisticated, targeting people of all ages. But with some knowledge, you can protect yourself and your loved ones.
Scammers stay scamming
Preventing being scammed is easier than getting money back after a scam. Here’s a quick guide to some of the most common scams out there today:
PIG BUTCHERING
In this long-term scam, cybercriminals build a relationship of trust over weeks or months through social media or dating apps. They often start with a seemingly mistake text. The scammers work to convince the victim to invest in a fake cryptocurrency or other get-rich-quick opportunities. Once they’ve “fattened up” the victim with the illusion of success, they disappear with the money.
GRANDPARENT SCAMS
This scam targets the elderly by impersonating a grandchild or relative in distress, often claiming to be in legal trouble or an emergency. Scammers ask for money urgently, usually through untraceable methods like wire transfers or gift cards.
ROMANCE SCAMS
Targeting people on dating platforms, scammers create fake profiles, build emotional connections, and ask for financial help, claiming emergencies, the need for airline tickets, or investment opportunities.
ACCIDENTAL DEPOSIT SCAMS Scammers pretend to mistakenly send you money via payment apps (like Venmo, Zelle, or PayPal) and then contact you to request it back. However, the original payment was made with a stolen or fake account, and returning it means you lose real money
TECH SUPPORT SCAMS
You get a call or pop-up alert claiming your computer is infected. The scammer, pretending to be from tech support, requests remote access to your device to “fix” the issue, stealing personal info or demanding payment for non-existent services.
UPS OR DELIVERY TEXT SCAMS
Scammers send a fake text message pretending to be from a delivery company like UPS, FedEx, or DHL, or the United States Postal Service. The message usually claims there’s an issue with your package and includes a link to “resolve” it. Clicking the link leads to a phishing site that tries to steal personal information or payment details.
How to Avoid Scams
These scams follow different playbooks, but if you watch out for red flags, you can avoid these scams and new ones that pop up!
- Never text back if the message was unexpected. Don’t even tell them they have the wrong number..
- Hang up and call back. If you receive an unexpected phone call from a loved one, law enforcement, or someone else claiming authority, hang up and call back through a number from your contacts list or verified through a web search.
- Have a safe word. Talk to your family and agree to a safe word or phrase that could be used if someone is distressed during a phone call. If you get an unsettling phone call from a loved one, ask for the safe word. Never post this information online or send it through text or email.
- Refuse to pay the suspicious way. Scammers generally request payment in forms like gift cards, crypto, or wire transfers, so any request to pay these ways is a red flag. ɯ Be wary on social media and dating apps. Know that scammers pose as genuine users on these platforms to connect with potential victims.
- Getting Out
If you suspect that you or someone you know is the victim of a scam, stop sending money immediately and end contact. The scammer might become threatening, angry, or attempt to make you feel guilty, but this is a persuasion technique and you have the power.
Don’t delete messages – take screenshots for evidence.
Report that you’re a victim of a scam to:
- Your bank or other financial institution
- ic3.gov
- Your local police department

Because this report is created in a booklet format we’re happy to print free copies for you.

