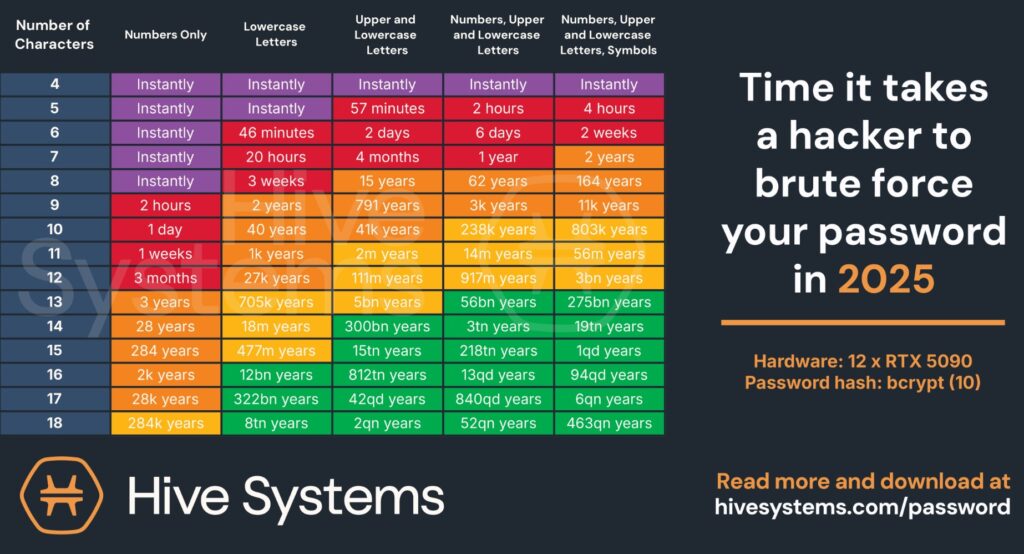
Since 2020, Hive Systems has been on a mission to crack the code – literally – on passwords. Their Hive Systems Password Table shows just how fast a hacker can brute-force your password… but what you see in the table is just the tip of the iceberg.
What is Brute Force?
A brute-force attack is when an attacker uses a set of predefined values to attack a target and analyze the response until they succeed. As you explore how to brute-force a password, remember that success depends on the size of the set of predefined values. If it is larger, it will take more time, but there is a better probability of success.
The most common — and simple — example of a brute-force attack is a dictionary attack. With this method, the attacker uses a password dictionary that contains millions of password options. The attacker tries these passwords one by one in successive attempts to satisfy the system’s authentication requirements. The attacker will succeed if the dictionary of options contains the correct password.
In a traditional brute-force attack, the attacker just tries a combination of letters and numbers to generate a password sequentially. However, this traditional technique will take much longer, especially with long passwords. These attacks can take several minutes to several hours or years, depending on the system used and the length of the password.
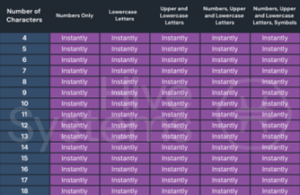
Stolen Passwords
What if my password has been previously stolen, uses simple words, or I reuse it between sites?”
The Hive Systems password table focuses on the idea that the hacker is working in a “black box” situation and is having to start from scratch to crack your hash to show the “worst case” or “maximum time required.” Most hackers will prioritize which words and strings of characters they’ll work on first through rainbow tables, dictionary attacks, and previously stolen hashes. If your password was part of another breach or uses dictionary words, then your password table looks like this:
BEST PRACTICES:
Strong password practices involve creating unique, lengthy passwords, ideally using passphrases or random character strings, and avoiding easily guessable information or common words. Unique passwords for each account are crucial, and password managers can help with storage and generation. Furthermore, enabling two-factor authentication adds an extra layer of security.
- Length is Key: While complexity was previously emphasized, current best practices prioritize password length, with NISTrecommending up to 64 characters.
- Passphrases or Random Strings: Create memorable phrases of 4-7 random words (passphrase) or use a mix of uppercase, lowercase, numbers, and symbols (random string).
- Avoid Personal Information: Do not include birthdays, names, or other easily guessable information in passwords.
- Unique Passwords: Use different passwords for each account to prevent a breach from affecting other accounts.
- Password Managers: Password managers can store and generate unique, strong passwords, making it easier to manage numerous accounts.
- Two-Factor Authentication: Enable two-factor authentication (MFA) whenever possible for added security.
- Don’t Re-use Passwords: Avoid reusing the same password for multiple accounts.
- Be Aware of Surroundings: Be cautious when entering passwords in public, especially on public Wi-Fi.
ACTSmart IT has been sharing The Hive Systems’ Password Table since it was first conceived in 2020.
It’s a great tool to get users to think about password security and to, hopefully, react with stronger passwords and other stronger security measures.
Resources:
https://www.hivesystems.com/blog/are-your-passwords-in-the-green
https://www.infosecinstitute.com/resources/hacking/popular-tools-for-brute-force-attack/

Would you like a print copy of this infographic mailed to you?
Simply fill out the form below